Does anybody know when/where/how the Text Edit tool is available to Claude? It's described here: https://docs.anthropic.com/en/docs/agents-and-tools/tool-use/text-editor-tool
Does anybody know when/where/how the Text Edit tool is available to Claude? It's described here: https://docs.anthropic.com/en/docs/agents-and-tools/tool-use/text-editor-tool

@ariadna & @ramin_hal9001 you two made me start the day with a smile you are the reason why I keep putting myself out there, in an era of AI garbage content, it is wonderful to talk and brainstorm with curious minds like yours.
Ariadna, I have been meaning to write a privacy-first web analytics service in #scheme, that would be a REST #api to store for example page view counts and more.
Ramin, what an awesome project, Schemacs, I saw a video on this in the past, kudos!!!
If you're rebuilding your API security stack, this is your north star.
Read more https://lttr.ai/Ag15M
Ich frag mal das Schwarmwissen: Weiß jemand warum beim Online-Shop der #api GmbH (Computer-Großhandel) alle Passwörter zurückgesetzt wurden?
https://www.borncity.com/blog/2025/07/24/passwort-reset-beim-api-online-shop-was-ist-das-los/

@Seemarc Ich frag einfach mal zurück und das Schwarmwissen: Weiß jemand warum beim Online-Shop der #api GmbH (Computer-Großhandel) alle Passwörter zurückgesetzt wurden?
https://www.borncity.com/blog/2025/07/24/passwort-reset-beim-api-online-shop-was-ist-das-los/

Ich frag mal das Schwarmwissen: Weiß jemand warum beim Online-Shop der #api GmbH (Computer-Großhandel) alle Passwörter zurückgesetzt wurden?
https://www.borncity.com/blog/2025/07/24/passwort-reset-beim-api-online-shop-was-ist-das-los/

I love that @readeck has a well documented API. It means that someone like me with rudimentary enough Python skills can do stuff. By stuff I mean send my Mastodon bookmarks to a Readeck collection and also work with them in bulk (operations like marking things as read and archiving)
Ne trouvant pas ce que je cherchais, j'ai développé un #plugin #wordpress qui capte les refs de #Discogs que l'on souhaite via son #API
Le plugin crée automatiquement le type de contenu (disque) avec ses taxonomies (style, type de support, label) et l'image cover par lot de 50 éléments.
Si vous avez 800 refs dans votre catalogue, cela prendra moins d'une heure de tout ramener. A la main, cela en demandera... beaucoup, beaucoup plus
Bref. Si vous êtes un #label, une distro... Je peux en dire plus >>
#Development #Explorations
A first look at the Interest Invoker API · Playing around with hover-triggered popovers https://ilo.im/165lbk
_____
#Tooltips #Popover #Invoker #API #Chrome #Browser #WebDev #Frontend #HTML #CSS

GitHub Spark: a nova aposta da Microsoft para criar apps com linguagem natural https://tugatech.com.pt/t69707-github-spark-a-nova-aposta-da-microsoft-para-criar-apps-com-linguagem-natural
From zero to infra or building a production-ready setup with our API and Ansible: Because our customers often run web applications, Tim wants to show in his blog post how services can be provided and managed with our API and other tools. You can read the rest of Tim's article here https://nine.ch/from-zero-to-infra-building-a-production-ready-setup-using-our-api-and-ansible/ on our website.
#infrastructure #production #ansible #api #blog #nine
Google lança o Gemini 2.5 Flash-Lite: velocidade máxima a um custo mínimo https://tugatech.com.pt/t69698-google-lanca-o-gemini-2-5-flash-lite-velocidade-maxima-a-um-custo-minimo

Latest Top Story on #HackerNews: AccuWeather to discontinue free access to Core Weather API
Original Story: https://developer.accuweather.com/new-portal
Author: TerribleTurnout
Score: 36
Number of Comments: 10
Posted At: 2025-07-23 19:26:42 UTC
URL: https://news.ycombinator.com/item?id=44663003
#api #hackernews #bot #hackernewsbot #news
I'm trying to figure out this API's deal
It has two bool fields both required: Has_Agreed and Has_Not_Agreed.
I assume they're trying to implement "User can either agree, disagree, or be in a state where they haven't yet decided"
But like... they could make the value of the boolean optional, so it's either true, false, or undefined. I know who wrote this and I know it's possible. Surely true/false/undefined is better than two separate booleans?!?
App Store : une nouvelle API pour convaincre les clients de ne pas se désabonner http://dlvr.it/TM4PJZ #AppStore #API
Please don't give away your Twitter API keys to Cloudinary
https://shkspr.mobi/blog/2023/07/please-dont-give-away-your-twitter-api-keys-to-cloudinary/
My CDN just asked me for all my Twitter API keys...
WTF? This would give them complete access to my app's Twitter account, the ability to send and receive messages, and anything else that my API key allows.
Giving them - or anyone - the entire set of credentials would be a very bad idea.
What's going on?
Twitter's slow-motion collapse and hostility to developers is causing a whole bunch of second-order effects.
Lots of services let people log in to them using Twitter. It is (was?!) a quick way to do identity management without having to bother the user with a separate username and password. Once someone has logged in, it's nice to be able to show their user avatar.
Annoyingly, Twitter never had a simple solution for that. You couldn't take my username - edent - and then grab twitter.com/edent/avatar.jpg. Instead, you had to perform an API call to get the image.
So a whole bunch of services started up which would retrieve Twitter avatars based on username. And they also did the same for Facebook, GitHub, Google, and lots of other OAuth providers.
I was using Cloudinary's Social Media Profile Pictures feature. But with Twitter's complete inability to serve API users, that functionality is going away.
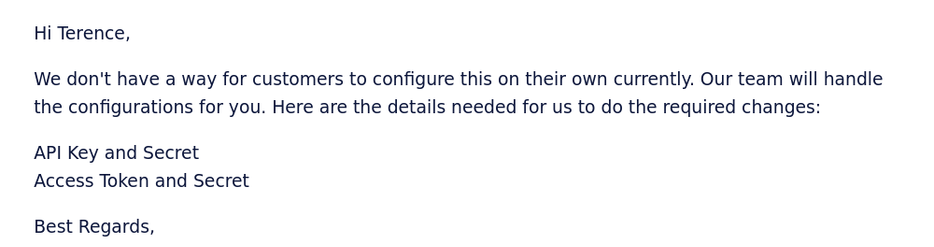
Last week Cloudinary said that they could keep the functionality going if I was willing to provide my API keys. I (somewhat impolitely) complained to Cloudinary that them asking for all the API keys was a security nightmare. They responded (politely) to my points:
I completely understand your concerns. Twitter's recent limitations to their API have made it so that we are unable to continue to use our own API credentials to allow customers to fetch Twitter assets, and so we must implement customer credentials instead. We were working on a long-term resolution, but they cut off our API access without warning, and so the temporary solution to minimise disruption was to request your credentials so our backend team can add in a rule to run your Twitter API requests with your own credentials. As such, we require both the API key and secret, along with the access token and secret.
...
As mentioned, this is just a temporary measure in order to ensure continued delivery of your assets. If you prefer to wait until we have a customer-facing portal to enter your Twitter account credentials, then you are certainly welcome to do so. Unfortunately I don't have an ETA on when such a solution might be available, however we will do our best to keep you updated.
I understand that they don't want users to have a degraded experience. And I understand that Twitter have screwed them over. And I'm sure that they're a thoroughly trustworthy company who will never get hacked. But asking customers to fatally compromise their own security like that is not acceptable.
Can't you just...?
Twitter doesn't offer a stable avatar service. Users can change their profile picture at any time, and the URl to the old image stops working. So caching the profile picture URl often leads to a broken image. Caching an old image can mean showing something outdated.
The API rate limits are pretty small for any service with heavy traffic.
Not showing a user image - or just the Twitter icon - could work. But it makes for a pretty crappy experience.
Telling everyone to leave Twitter and join Mastodon would be nice.
Creating a bespoke read-only API key could work - but Twitter now limits the number of apps a develop can have unless they pay stupid money.
It is entirely understandable that people would panic and hand over the keys to their (digital) kingdom. Fear makes people do dangerous things.
Anyway, this Mastodon post sums it up the best:
Post by @RickiTarr View on Mastodon
Publico un nuevo artículo: «Construyendo APIs RESTful robustas con Arquitectura Limpia y Hypermedia»
https://andros.dev/blog/f3521f7e/construyendo-apis-restful-robustas-con-arquitectura-limpia-y-hypermedia/
#api #arquitectura #rest #restful #anuncio
"Drawing from the latest research and implementation playbooks, this post explores a comprehensive and modernized approach to API threat detection and response, rooted in pragmatic security engineering and continuous evolution." https://lttr.ai/AgwhV