#clickfix
Szczegółowa analiza techniczna nowej kampanii ukierunkowanych ataków wykorzystujących metodę #ClickFix w celu dostarczenia złośliwego oprogramowania, przygotowana przez Irka Tarnowskiego, który swego czasu napisał sporo dobrych tekstów do @zaufanatrzeciastrona
A detailed technical analysis of a new campaign of targeted attacks using the ClickFix method to deliver malware
#ClickFix went from virtually non-existent to the second most common attack vector blocked by #ESET, surpassed only by #phishing. This novel social engineering technique accounted for nearly 8% of all detections in H1 2025. #ESETresearch
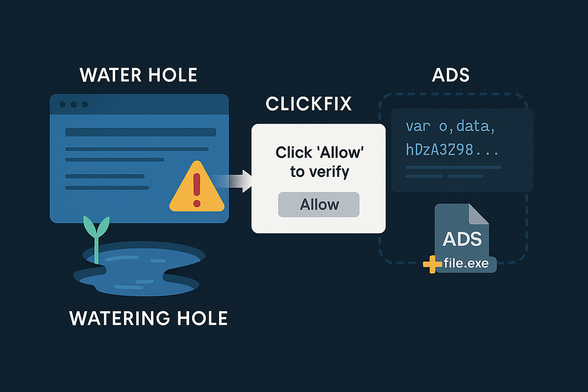
ClickFix lures users by displaying bogus error messages followed by quick fix instructions, including copy-pasting malicious code. Running the code in the victim’s command line interpreter delivers malware such as #RATs, infostealers, and cryptominers.
Between H2 2024 and H1 2025, ESET’s detection for ClickFix, HTML/FakeCaptcha, skyrocketed by 517%. Most detections in ESET telemetry were reported from Japan (23%), Peru (6%), and Poland, Spain, and Slovakia (>5% each).
What makes #ClickFix so effective? The fake error message looks convincing; instructions are simple, yet the copied command is too technical for most users to understand. Pasting it into cmd leads to compromise with final payloads, including #DarkGate or #LummaStealer.
While #ClickFix was introduced by cybercriminals, it’s since been adopted by APT groups: Kimsuky, Lazarus; Callisto, Sednit; MuddyWater; APT36. NK-aligned actors used it to target developers, steal crypto and passwords from Metamask and #macOS Keychain.
#ClickFix uses psychological manipulation by presenting fake issues and offering quick solutions, which makes it dangerously efficient. It appears in many forms – error popups, email attachments, fake reCAPTCHAs – highlighting the need for greater vigilance online.
Read more in the #ESETThreatReport: https://welivesecurity.com/en/eset-research/eset-threat-report-h1-2025
@filippo the copy/paste technique is called #ClickFix . the site in the image is infected by TA2726's Keitaro which is well known for sending Windows folks to #SocGholish . what they do with macOS folks has changed over the years. i see they sent you to something that delivered what looks like Poseidon Stealer.
https://medium.com/@MateoPappa/letsdefend-poseidon-macos-stealer-hard-a796c85d8c72

2025-07-15 (Tuesday): Tracking #SmartApeSG
The SmartApeSG script injected into page from compromised website leads to #ClickFix style fake verification page. ClickFix-ing you way through this leads to a #NetSupportRAT infection.
Compromised site (same as yesterday):
- medthermography[.]com
URLs for ClickFix style fake verification page:
- warpdrive[.]top/jjj/include.js
- warpdrive[.]top/jjj/index.php?W11WzmLj
- warpdrive[.]top/jjj/buffer.js?409a8bdbd9
Running the script for NetSupport RAT:
- sos-atlanta[.]com/lal.ps1
- sos-atlanta[.]com/lotu.zip?l=4773
#NetSupport RAT server (same as yesterday):
- 185.163.45[.]87:443
I finally stumbled upon a real #ClickFix attack in the wild. My favorite weather page presented the screen as shown. It doesn't take much tech knowledge to know these instructions are pure bullshit.
Now here's what's interesting. I reloaded the page, normal page came up. Cleared the cookies, normal page. Tried a different browser, normal page. So is it random? Should I alert the site owner?
2025-07-14 (Monday): #SmartApeSG script injected into page from compromised website leads to #ClickFix style fake verification page. ClickFix-ing you way through this leads to a #NetSupportRAT infection.
Compromised site:
- medthermography[.]com
URLs for ClickFix style fake verification page:
- lebensversicherungvergleich[.]top/jjj/include.js
- lebensversicherungvergleich[.]top/jjj/index.php?OtKXgPVX
- lebensversicherungvergleich[.]top/jjj/buffer.js?4261984971
Running the script for NetSupport RAT:
- affordableasphalt-paving[.]com/lal.ps1
- affordableasphalt-paving[.]com/lotu.zip?l=3526
#NetSupport RAT server:
- 185.163.45[.]87:443
New Interlock RAT Variant Distributed via FileFix Attacks https://www.securityweek.com/new-interlock-rat-variant-distributed-via-filefix-attacks/ #Malware&Threats #Ransomware #InterLock #ClickFix #FileFix #RAT
New Interlock RAT Variant Distributed via FileFix Attacks https://www.securityweek.com/new-interlock-rat-variant-distributed-via-filefix-attacks/ #Malware&Threats #Ransomware #InterLock #ClickFix #FileFix #RAT
In May 2025, #ESET participated in operations that largely disrupted the infrastructure of two notorious infostealers: #LummaStealer and #Danabot.
As part of the Lumma Stealer disruption effort, carried out in conjunction with Microsoft, BitSight, Lumen, Cloudflare, CleanDNS, and GMO Registry, ESET supplied technical analysis and statistical information.
Danabot was targeted by the #FBI and #DCIS, alongside #OperationEndgame led by #Europol and #Eurojust. ESET participated together with several other companies. We provided the analysis of the malware’s backend infrastructure and identified its C&C servers.
Before these takedowns, both infostealers were on the rise: in H1 2025, Lumma Stealer detections grew by 21%, while Danabot’s numbers increased by more than 50%.
For a time, Lumma Stealer was the primary payload of HTML/FakeCaptcha trojan, used in the #ClickFix social engineering attacks that we also cover in this issue of the #ESETThreatReport. In recent months, we have seen Danabot being delivered via ClickFix as well.
For more details on these two operations and on the ClickFix attacks, read the latest #ESETThreatReport: https://welivesecurity.com/en/eset-research/eset-threat-report-h1-2025
ClickFix = CAPTCHA + Malware
Rhadamanthys infostealer is back, this time hiding behind fake “verify” prompts that run PowerShell.
No macros. No attachments. SMEs are targets.
#CyberSecurity #ClickFix #Rhadamanthys #PaxionCyber #SMBSecurity #CyberAwareness
@badsamurai That's basically my point. #FileFix is just #ClickFix by another name. Trying to separate the two doesn't make sense to me.
Definitely agree that your mitigation is a good way to help combat this.
Example 2: #FileFix
As of 2025-07-03, the #KongTuke campaign is using FileFix style #ClickFix pages to distribute whatever this campaign is distributing.
It's likely pushing #InterlockRAT based on previous discussions I've had here, but I couldn't confirm, because it didn't like me.
Example 1: #RunFix
As of 2025-07-03, the #SmartApeSG campaign is using RunFix style #ClickFix pages to distribute #NetSupportRAT
#ClickFix is a social engineering technique that uses fake verification pages and clipboard hijacking to convince people to click and keyboard stroke their way to an infection. So let's categorize #FileFix properly in the pantheon of ClickFix Attacks.
FileFix: A ClickFix page that asks you to past script into a File Manager window.
#RunFix: A ClickFix page that asks you to paste script into a Run window
#TermFix: A ClickFix page that asks you to paste script into a terminal window (cmd.exe console or PowerShell terminal).
We cool with that? Any others types I'm missing?
How this ClickFix campaign leads to Redline Stealer
#ClickFix #RedLineStealer
https://sec.okta.com/articles/2025/07/how-this-clickfix-campaign-leads-to-redline-stealer/

ClickFix Spin-Off Attack Bypasses Key Browser Safeguards – Source: www.darkreading.com https://ciso2ciso.com/clickfix-spin-off-attack-bypasses-key-browser-safeguards-source-www-darkreading-com/ #rssfeedpostgeneratorecho #DarkReadingSecurity #CyberSecurityNews #DARKReading #ClickFix



