SMBs using Simple Car Rental System 1.0 face a public, low-severity XSS flaw in add_vehicles.php via the car_name field. Quick ROI: apply vendor patch or input validation, add WAF rules, train admin staff. #Cybersecurity #SMB #XSS

SMBs using Simple Car Rental System 1.0 face a public, low-severity XSS flaw in add_vehicles.php via the car_name field. Quick ROI: apply vendor patch or input validation, add WAF rules, train admin staff. #Cybersecurity #SMB #XSS

CVE-2025-46199: CRITICAL XSS in Grav CMS ≤1.7.48 allows remote attackers to inject scripts via form fields—no auth or user interaction needed. Patch when available, enforce WAF/CSP! https://radar.offseq.com/threat/cve-2025-46199-na-4c605828 #OffSeq #XSS #GravCMS #Vuln
Cybercrime Forum XSS Returns on Mirror and Dark Web 1 Day After Seizure – Source:hackread.com https://ciso2ciso.com/cybercrime-forum-xss-returns-on-mirror-and-dark-web-1-day-after-seizure-sourcehackread-com/ #1CyberSecurityNewsPost #CyberSecurityNews #cybersecurity #CyberCrime #Hackread #security #DarkNet #DarkWeb #Europol #Ukraine #France #XSS
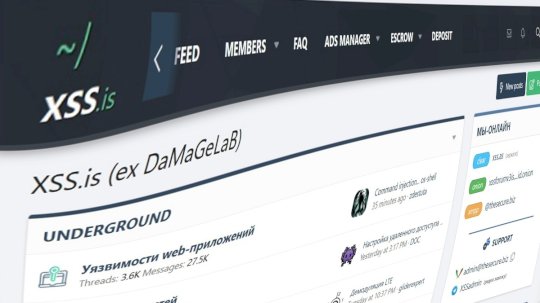
Cybercrime Forum XSS Returns on Mirror and Dark Web 1 Day After Seizure https://hackread.com/cybercrime-forum-xss-returns-mirror-dark-web-seizure/ #Cybersecurity #CyberCrime #Security #DarkWeb #DarkNet #darkweb #Europol #Ukraine #France #XSS

New: Just a day after its seizure and admin arrest, cybercrime forum #XSS is back online via its mirror and dark web domains... but with many questions, rumors and a lack of trust.
Read: https://hackread.com/cybercrime-forum-xss-returns-mirror-dark-web-seizure/

Fórum de Cibercrime XSS: A Volta do Perigo na Dark Web!
Um novo fórum de cibercrime, focado em ataques XSS, está ganhando destaque na dark web após um recente ataque. Descubra como esses grupos operam e as implicações para a segurança cibernética. Não fique desinformado sobre as ameaças que podem afetar seus dados! Clique para saber mais e se proteger!
.
.
#Cibersegurança #XSS #DarkWe...
https://inkdesign.com.br/forum-de-cibercrime-xss-reemerge-em-dark-web-apos-ataque/?fsp_sid=100552
Suspected Admin of XSS.IS Cybercrime Forum Arrested in Ukraine – Source:hackread.com https://ciso2ciso.com/suspected-admin-of-xss-is-cybercrime-forum-arrested-in-ukraine-sourcehackread-com/ #1CyberSecurityNewsPost #CyberSecurityNews #cybersecurity #CyberCrime #DaMaGeLaB #Hackread #Europol #Ukraine #France #Russia #XSSIS #XSS

Suspected Admin of XSS.IS Cybercrime Forum Arrested in Ukraine https://hackread.com/suspected-xss-is-admin-cybercrime-forum-arrest-ukraine/ #Cybersecurity #CyberCrime #DaMaGeLaB #Europol #Ukraine #France #Russia #XSSIS #XSS

The Russian language cybercrime forum #XSS has been seized after its suspected admin was arrested in #Ukraine, however its dark web and mirror domains only show a 504 Gateway Timeout error.
Read: https://hackread.com/xss-is-cybercrime-forum-seized-ukraine-arrested-admin/

France Says Administrator of Cybercrime Forum XSS Arrested in Ukraine https://www.securityweek.com/france-says-administrator-of-cybercrime-forum-xss-arrested-in-ukraine/ #Tracking&LawEnforcement #hackerforum #Cybercrime #cybercrime #arrested #France #forum #XSS
Suspected admin of XSS.IS, one of the most notorious Russian-language cybercrime forums, has been arrested in Ukraine.
Read: https://hackread.com/suspected-xss-is-admin-cybercrime-forum-arrest-ukraine/

Seamless remote browser session control demonstrating the impact of XSS without the need for stealing cookies (weaponized adaptation of the OpenReplay project)
Missed one of my past conference talks? Let’s fix that.
I’m sharing my favorites—packed with real-world advice, lessons, and a few laughs.
“XSS Deep Dive” https://twp.ai/4invfx
Many thanks to @xoreipeip for presenting his talk "Server-Side Cross-Site Scripting" #XSS at the #OWASPLondon Chapter meetup last week!
The video recording of the talk is now available to watch on our YouTube channel [PLEASE SUBSCRIBE!]:
https://youtu.be/UNoUEBNhRjE
Реализация RCE-атаки на сервер. Указанный подход не логируется nginx/Apache и легко ускользает от глаз админа.
- Вставка XSS-пейлоада в поле профиля, расчёт на срабатывание в интерфейсе администратора.
- Администратор открывает панель, пейлоад выполняется и отправляет куки/информацию злоумышленнику через его XSS-инфраструктуру.
- Используя добытые данные (например, токен сессии), атакующий получает доступ к админке веб-приложения.
- Через административную панель он загружает shell.php с простым PHP-обработчиком команды через $_GET.
- Далее попытка прямой передачи команды в URL (например, ?cmd=whoami), сервер заблокировал вызов или обрезал параметр.
- Модификация оболочки для выполнения команды из заголовка Accept-Language.
- Далее отправляется запрос с заголовком Accept-Language: id; cat /etc/passwd и получается вывод команды.
Доступ к файлам, выполнение системных команд и т.д.
Подробности в статье (https://is4curity.medium.com/from-blind-xss-to-rce-when-headers-became-my-terminal-d137d2c808a3).

CISA Releases 3 ICS Advisories Covering Vulnerabilities and Exploits https://cybersecuritynews.com/cisa-releases-3-ics-advisories/ #CyberSecurityNews #cybersecuritynews #Vulnerabilities #CyberSecurity #cybersecurity #XSS

Ex US Soldier Cameron Wagenius Guilty in Telecom Hacking and Extortion https://hackread.com/us-soldier-cameron-wagenius-guilty-telecom-hacking-extortion/ #CameronWagenius #Cybersecurity #BreachForums #UnitedStates #CyberCrime #Extortion #hacking #Telecom #Verizon #AT&T #XSS
