Learn how Full Disk Encryption with LUKS and NBDE protects your data at rest and automates secure boot on Linux systems. https://hackernoon.com/securing-data-at-rest-from-luks-to-nbde-a-modern-encryption-guide #dataencryption

Learn how Full Disk Encryption with LUKS and NBDE protects your data at rest and automates secure boot on Linux systems. https://hackernoon.com/securing-data-at-rest-from-luks-to-nbde-a-modern-encryption-guide #dataencryption

Analysis of the latest Mirai wave exploiting TBK DVR devices with CVE-2024-3721 – Source: securelist.com https://ciso2ciso.com/analysis-of-the-latest-mirai-wave-exploiting-tbk-dvr-devices-with-cve-2024-3721-source-securelist-com/ #Vulnerabilitiesandexploits #rssfeedpostgeneratorecho #Secureenvironment(IoT) #MalwareTechnologies #CyberSecurityNews #internetofthings #vulnerabilities #DataEncryption #GReATresearch #securelistcom #Honeypot #botnets #Malware #LINUX #Mirai #CVE #RC4

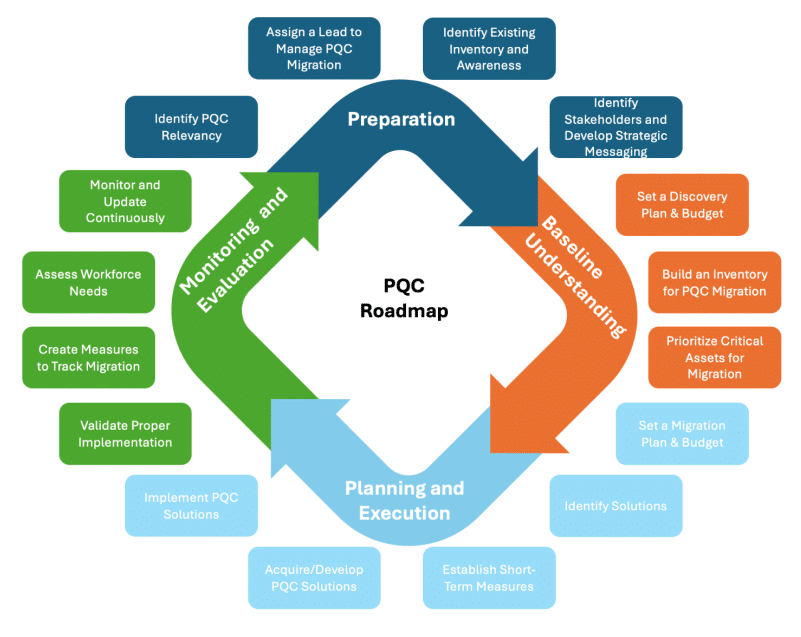
Post-Quantum Cryptography Migration Should Start Now: Coalition https://thecyberexpress.com/post-quantum-cryptography-migration/ #postquantumcryptography #TheCyberExpressNews #TheCyberExpress #DataEncryption #FirewallDaily #cybersecurity #RSAencryption #postquantum #Encryption #CyberNews
Warden Encoder V1 & V2
Encrypt, obfuscate, and protect your code. Power meets simplicity: https://wardenshield.com/warden-encoder-v1-and-v2
#CodeSecurity #encryption #EncryptionTools #wardenshield #Cybersecurity #cybertools #infosec #ZeroTrust #endpointsecurity #dataencryption #DigitalDefense #ransomwareprotection

#autonomoussystems #Bufferoverflow #connecteddevices #Crosssitescripting(XSS) #cyberattacks #cybersecurity #dataencryption #Dataprivacy #DenialofService(DoS) #deviceencryption #dosattack #hacking #hackinglot #InternetofThings #iOT #IoTpreventionmethods #IoTrisks #IoTSecurity #IoTvulnerabilities #lot #lotdevices #malware #networksecurity #outdatedprotocols #Physicaltampering #Privacybreaches #secureiot
https://miltonmarketing.com/news/hacking-the-iot-vulnerabilities-and-prevention-methods/
State of ransomware in 2025 – Source: securelist.com https://ciso2ciso.com/state-of-ransomware-in-2025-source-securelist-com/ #rssfeedpostgeneratorecho #APT(Targetedattacks) #Crossplatformmalware #CyberSecurityNews #MalwareStatistics #Financialthreats #MicrosoftWindows #Targetedattacks #DataEncryption #securelistcom #Publications #ransomware #Lockbit #BYOVD #RaaS #APT #LLM #AI

Cutting-Edge Cyber Technology for Enhanced Security
Empower your business with advanced cyber technology solutions from E Shield IT Services. Our services include AI-driven threat detection, data encryption, and next-gen security frameworks to keep your organization safe from cyber risks.
Protecting sensitive data has never been easier! Actifile’s managed data security helps with CUI discovery & dynamic encryption.
https://taraskovalenko.github.io/posts/mongodb-encryption/
Encryption in MongoDB: Why I Switched to Another Database

#QuantumComputing by harnessing quantum mechanics to process information at unprecedented speeds, is driving advancements in encryption
, machine learning
, and solving complex problems
.
Dive into how quantum computing is set to reshape the future of IT & AI, unlocking new possibilities and efficiencies.
Read our blog for in-depth insights!
https://neuronus.net/en/blog/quantum-computing-a-revolution-in-it-and-ai
What Cybersecurity Can Teach Us About the Human Body https://thecyberexpress.com/cybersecurity-about-the-human-body/ #CybersecurityInfographic #IntrusionDetectionSystem #SecurityOperationsCenter #TheCyberExpressNews #CyberEssentials #TheCyberExpress #DataEncryption #FirewallDaily #HumanBody #firewall

**DEX Exchange: What It Is and How to Get Started**
Decentralization is one of the key principles of the crypto industry, so it's no surprise that the popularity of De-Fi and decentralized exchanges (DEX) has been growing for several years. In this article, Trustee specialists will explain what decentralized cryptocurrency exchanges are, how they are regulated, how they differ from centralized exchanges, and how to start using them. Read on for an overview of their advantages and disadvantages, predicted future prospects, and a ranking of the best decentralized exchanges!
### What Is a DEX Exchange?
A decentralized exchange (DEX) is a platform for exchanging digital assets that operates based on decentralization—without central governance by an individual or group of people and without a central node or server.
Essentially, a DEX is a blockchain-based platform that facilitates peer-to-peer (P2P) transactions without intermediaries. It does not store user personal data or their financial information on its servers. Users exchange assets through smart contracts and algorithms based on a distributed ledger.
Many exchanges that call themselves decentralized actually store trading data and user order information on their servers, even though they do not hold private keys. The first efforts to create cryptocurrency DEXs emerged in 2014, but significant development only started in 2018.
### Regulation of DEXs
Governments have mixed opinions on financial-technology platforms that are governed solely by their user communities, with no central entity accountable for transactions.
As with cryptocurrency in general, authorities in different countries have not reached a consensus. For example, Singapore’s regulator seeks to develop a regulatory framework specifically for DEXs, while the U.S. attempts to apply existing laws.
In most countries, decentralized exchanges remain unregulated as they are not tied to any legal entities. This means that in case of violations, there is no single entity to hold accountable or to send official requests.
### How DEXs Work
Orders are executed on the blockchain using smart contracts. User funds remain on their own devices. While decentralized exchanges operate on various blockchains, the most popular ones use Tron, Ethereum, and Binance Chain.
A DEX serves as a marketplace for matching buy and sell orders. Once orders are matched, trading occurs directly between users.
### Pros and Cons of DEXs
**Advantages** | **Disadvantages**
--- | ---
No central governing authority; operates automatically or with community governance | No official customer support
Completely anonymous transactions | Difficulties converting fiat currencies
Secure data storage | Complex user interface, challenging for beginners
No need for user identification (KYC/AML) | No data recovery options for users
Fair pricing with no market manipulation | Trading limited to tokens that support smart contracts
Regulators cannot freeze accounts | Smaller liquidity pools compared to centralized exchanges
Transparent transactions | Limited functionality (e.g., no margin trading, stop-loss orders, leverage)
No counterparty risks | Potential smart contract vulnerabilities
Ability to trade tokens not listed on centralized exchanges | Slower trading speeds compared to centralized exchanges
No single point of failure |
### Differences Between Decentralized and Centralized Exchanges
The main difference is the absence of a central governing entity that controls user data and exchange operations. In DEXs, governance is automated or semi-automated, with community involvement in decision-making.
DEXs are more suitable for experienced traders. Users manage their own funds and trades without access to customer support or fund recovery options. While this ensures full control, it also places sole responsibility on the user. However, all transactions are fully transparent, as all activity can be tracked on the blockchain.
Centralized exchanges (CEXs) have tools for market manipulation and can freeze user accounts at any time due to "suspicious" activity. Additionally, since CEXs have legal addresses, government authorities in some jurisdictions can seize their assets, confiscate servers, and freeze user accounts. These actions are not possible on DEXs because their servers are distributed across various locations, placing them in a legal gray area.
### Examples of Decentralized Exchanges
The number of DEX platforms has significantly increased in recent years. Below are some of the most popular and highly rated decentralized cryptocurrency exchanges.
- **JustSwap** – A decentralized trading protocol on TRON for automated liquidity provision.
- **IDEX** – A real-time DEX for ERC-20 tokens on Ethereum with hardware wallet support and the ability to cancel orders without fees.
- **Waves DEX** – A cross-platform exchange built on the Waves blockchain that allows trading token pairs without needing an intermediary currency.
- **PancakeSwap** – A DEX on Binance Smart Chain (BSC) that supports BEP-20 token trading, liquidity rewards, and features NFT collections and lotteries.
- **Bancor Network** – A decentralized exchange with automatic pricing and no price difference between buy and sell orders.
- **Binance DEX** – A decentralized counterpart to Binance’s main exchange.
- **Uniswap** – A decentralized exchange on Ethereum featuring an automated liquidity protocol.
Decentralized exchanges are a cornerstone of the DeFi movement, offering enhanced security, transparency, and user control. However, they also present usability challenges and require users to take full responsibility for their funds. Understanding how DEXs operate and their key differences from centralized exchanges is essential for making informed decisions in crypto trading.
Here are 23 hashtags that you can use depending on the context or content you are sharing:
#technology
#security
#cryptocurrency
#privacy
#AI
#machinelearning
#innovation
#websecurity
#cybersecurity
#digitalprivacy
#virtualmachines
#linux
#wordpress
#cloudhosting
#internetofthings
#networking
#open-source
#cyberattack
#blockchain
#cryptotrading
#anonymity
#dataencryption
#futuretech
Let me know if you have a specific theme, and I can tailor the hashtags accordingly!
How can we protect the integrity and confidentiality of the footage from body-worn cameras in law enforcement and public safety?
@alexlomas has outlined how encryption, integrity verification, and security measures can protect these devices so that the footage remains reliable: https://www.pentestpartners.com/security-blog/how-to-secure-body-worn-cameras-and-protect-footage-from-cyber-threats/
Secure Your Secrets: Unveiling the Power of dotfile-locker for Sensitive Configuration Management
In a world where data privacy is paramount, managing sensitive configuration files has become a crucial task for developers and professionals alike. Enter dotfile-locker, a revolutionary tool that sim...
### Applied Murphy's Laws for Cryptography (Loose Interpretation)
1. **Law of Encryption Complexity:**
The more complex the encryption algorithm, the faster someone will find a simple way to break it.
2. **Law of Limited Time:**
When there's no time to generate the perfect key, "1234" becomes the default password.
3. **Law of Trust:**
The greatest vulnerability in any cryptosystem is the person using it.
4. **Law of Privacy Illusion:**
The moment you feel completely anonymous, someone will access your metadata.
5. **Law of the Forgotten Key:**
If a private key is created and perfectly secured, you’ll lose access to it at the worst possible moment.
6. **Law of Overconfidence:**
"This algorithm is unbreakable" — until a student proves otherwise in their thesis.
7. **Developer’s Law:**
The best cryptographic solution you design will be broken by your own testing team.
8. **Law of Universality:**
The more universal the crypto algorithm, the more exposed it is to attacks on its weak points.
9. **Law of Resource Economy:**
Every cryptosystem is a compromise between security and performance, but breaking it will always be faster.
10. **Law of Government Interference:**
If your algorithm is good enough to thwart hackers, regulators will demand a backdoor.
11. **Law of the Attacker:**
Your cryptography is never too complex for a hacker, but always too complex for the average user.
12. **Law of Unforeseen Flaws:**
Every algorithm has a vulnerability, but you'll discover it only when it's too late.
13. **Law of Urgent Updates:**
The moment you deploy a new cryptosystem, its algorithm becomes outdated by current standards.
14. **Law of Retrospect:**
"No one will break RSA in our lifetime" — until quantum computers prove otherwise.
15. **Law of Entropy:**
The more complex the password, the more likely the user is to write it on a sticky note and attach it to their monitor.
16. **Law of Crypto-Anarchy:**
The more secure your system, the more it annoys governments and corporations.
17. **Law of Simplicity:**
If something in cryptography looks too simple to be broken, it's already been compromised.
18. **Key Length Law:**
The moment you double the key length, someone finds an attack that breaks both the old and new versions.
19. **Law of Paranoia:**
In cryptography, you’re either not paranoid enough or already too late.
20. **Law of the Last Test:**
The biggest vulnerability will be discovered one minute after the system goes live.
---
### **Hashtags (23):**
#MurphysLaw #Cryptography #CyberSecurity #Encryption #DataProtection #Privacy #DigitalSecurity #CryptoFails #QuantumComputing #Hacking #PasswordSecurity #CryptographicAlgorithms #CyberThreats #DataEncryption #KeyManagement #ParanoiaInSecurity #UnbreakableCode #SecurityFlaws #BackdoorThreat #ITHumor #TechAnarchy #StickyNotePasswords #QuantumThreats #cryptoinsights
Nitrogen Ransomware Attacks Encrypts Files With .NBA Extension https://cybersecuritynews.com/nitrogen-ransomware-attacks-organizations/ #LatestCyberThreatsNews #CyberSecurityNews #DataEncryption #cybersecurity #Ransomware #ransomware
The Importance of Cybersecurity in Protecting Sensitive Financial Data
#CybersecurityMatters #ProtectYourData #FinancialSecurity #CyberThreats #IdentityTheftProtection #SecureBanking #DataEncryption #NetworkSecurity #AdvancedCybersecurity #EmergingRisks #DataProtection #RiskManagement #CyberAwareness
Cybercriminals exploit vulnerabilities, causing financial losses and identity theft while damaging reputations and leading to compliance issues for financial institutions.
https://commercestheories.com/2024/12/24/the-importance-of-cybersecurity-in-protecting-sensitive-financial-data/

𝐓𝐋𝐒 𝐯𝐬. 𝐒𝐒𝐋
Understanding the difference is crucial for securing your data in transit. TLS is the modern, secure standard, while SSL is outdated and vulnerable.
Register here for cybersecurity training- https://www.infosectrain.com/cybersecurity-certification-training/
Celebrating the International Day of Computer Science!
From pioneers like Grace Hopper to modern advancements in data security, computer science shapes our world.
At Cryptomator, we enable secure cloud encryption to protect privacy and empower the digital future.
How has computer science impacted your life? Let us know!
Ymir: new stealthy ransomware in the wild – Source: securelist.com https://ciso2ciso.com/ymir-new-stealthy-ransomware-in-the-wild-source-securelist-com/ #rssfeedpostgeneratorecho #MalwareDescriptions #MalwareTechnologies #CyberSecurityNews #IncidentResponse #DataEncryption #Windowsmalware #securelistcom #Trojanstealer #PowerShell #ransomware #Malware #Trojan
