iX-Workshop IT-Sicherheit: Pentests methodisch planen, anfordern und analysieren
Schritt für Schritt zum sicheren System: Penetrationstests methodisch planen, beauftragen und auswerten, um Schwachstellen in der eigenen IT aufzuspüren.

iX-Workshop IT-Sicherheit: Pentests methodisch planen, anfordern und analysieren
Schritt für Schritt zum sicheren System: Penetrationstests methodisch planen, beauftragen und auswerten, um Schwachstellen in der eigenen IT aufzuspüren.

Check out our complete guide to Mobile App VAPT—a deep dive into why penetration testing is essential for keeping your apps secure and your users safe.
Read more: https://www.ecsbiztech.com/mobile-app-vapt-complete-guide-to-mobile-application-penetration-testing/
#MobileAppSecurity #VAPT #PenetrationTesting #AppSecurity #CyberDefense
Cervantes: Open-source, collaborative platform for pentesters and red teams https://www.helpnetsecurity.com/2025/07/23/cervantes-open-source-collaborative-platform-pentesters-red-teams/ #penetrationtesting #cybersecurity #opensource #Don'tmiss #software #redteam #GitHub #OWASP #News

CORSO "ACTIVE DIRECTORY PENETRATION TEST". APERTE LE PRE ISCRIZIONI E AVVIATA LA PROMO
OFFERTA ESCLUSIVA entro il 31 AGOSTO! -15% sul prezzo già scontato del corso (in quanto è la prima live class su questo argomento) a chi effettua la pre-iscrizione entro l 31 di Agosto!
Informazioni di dettagli del corso: Per info e iscrizioni scrivi a formazione@redhotcyber.com oppure su WhatsApp al 393791638765 https://www.redhotcyber.com/servizi/academy/live-class-active-directory-ethical-hacking/
Per info e iscrizioni scrivi a formazione@redhotcyber.com oppure su WhatsApp al 393791638765
Diventa un ethical hacker professionista ora! Non perdere tempo!
“A 250-page vuln report is useful for no one.”
That’s how Elpha Secure’s CTO summed up their reality before using Pentest-Tools.com. And we can totally understand!
Scattered tools and noise-heavy reports made scaling painful. Now, their team gets:
Fast, automated assessments
Results they can trust
Reports that actually help clients make informed decisions
Read the key takeaways here → https://pentest-tools.com/case-studies/elpha-secure

Leaked and Loaded: DOGE’s API Key Crisis
One leaked API key exposed 52 private LLMs and potentially sensitive systems across SpaceX, Twitter, and even the U.S. Treasury.
In this episode of Cyberside Chats, @sherridavidoff and @MDurrin break down the DOGE/XAI API key leak. They share how it happened, why key management is a growing threat, and what you should do to protect your organization from similar risks.
Watch the video: https://youtu.be/Lnn225XlIc4
Listen to the podcast: https://www.chatcyberside.com/e/api-key-catastrophe-when-secrets-get-leaked/
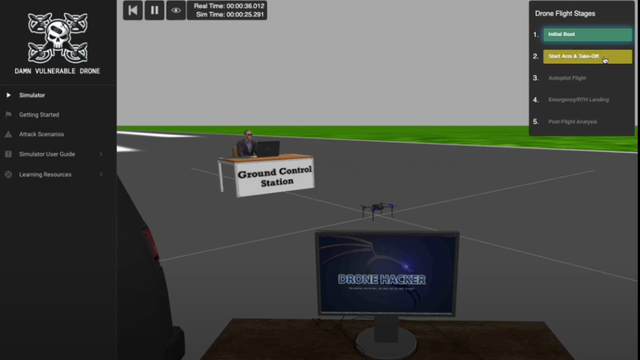
A Vulnerable Simulator for Drone Penetration Testing - The old saying that the best way to learn is by doing holds as true for penetrati... - https://hackaday.com/2025/07/18/a-vulnerable-simulator-for-drone-penetration-testing/ #penetrationtesting #securityhacks #dronesecurity #dronehacks #security #drone
Stay ahead of cyber threats! Discover how VAPT Services in India can safeguard your business from vulnerabilities.
Read the blog: https://www.ecsbiztech.com/a-comprehensive-guide-to-vulnerability-assessment-penetration-testing-vapt-services-in-india/
#VAPT #CyberSecurity #VAPTServices #PenetrationTesting #CyberThreatProtection
How do attackers go from file shares to full domain admin access without ever stealing a password? In this real-world case study, we'll share how a single misconfiguration opened the door to a full network compromise, and how our #pentest team exploited hidden file shares (with that sneaky $ at the end) to uncover sensitive data most IT teams don’t realize is exposed.
We'll share:
• How attackers exploit hidden file shares
• Why misconfigured Windows Deployment Services are a major risk
• The exact relay attack path that led to domain dominance
• What red flags to look for in your environment
Watch: https://youtu.be/78L2Zz2Ttbs
Putting AI-assisted ‘vibe hacking’ to the test – Source: www.csoonline.com https://ciso2ciso.com/putting-ai-assisted-vibe-hacking-to-the-test-source-www-csoonline-com/ #rssfeedpostgeneratorecho #ArtificialIntelligence #PenetrationTesting #CyberSecurityNews #vulnerabilities #cyberattacks #CSOonline #CSOOnline

Is autonomous pen testing the future of offensive security or just a flashy concept?
Join us on the Shared Security Podcast as we discuss XBOW's game-changing technology with co-host Kevin Johnson and explore what it means for cybersecurity professionals.
Watch on YouTube:
https://youtu.be/VeOMYBSk3Dk
Listen and subscribe to the podcast!
https://sharedsecurity.net/subscribe
Exposure management is the answer to: “Am I working on the right things?” https://www.helpnetsecurity.com/2025/07/08/dan-decloss-plextrac-exposure-management-strategy/ #vulnerabilitymanagement #penetrationtesting #incidentresponse #cybersecurity #Don'tmiss #Features #Hotstuff #PlexTrac #strategy #News

Your UPS might be a silent security risk.
Watch our new video to see how a standard uninterruptible power supply (UPS) became the gateway to hacking a real bank.
We walk you through:
How UPS devices connect to networks—and why that matters
The danger of default credentials on embedded systems
How spoofed email servers let attackers steal domain credentials
The exact steps that led to full network compromise
Watch now! https://youtu.be/Ru5RR9COqYw
Certified.
Trusted.
Proactive.
Check Point’s Infinity Platform Service Pen Testing is now CREST-accredited — a global gold standard in ethical hacking!
Why it matters: Real-world attack simulations
Expert-led assessments
Tested, proven, and now certified by CREST
Because in cyber security, you don’t wait for threats — you hunt them first. https://blog.checkpoint.com/infinity-global-services/raising-the-bar-infinity-global-services-pen-testing-achieves-crest-accreditation/
New mass scanning activity may be the first step in another MOVEit attack.
Hackers are actively scanning the internet for exposed MOVEit systems—hundreds of unique IPs every day—suggesting the early stages of coordinated exploitation.
Threat intel firm GreyNoise warns this is the same pattern seen weeks before past mass attacks. Known MOVEit vulnerabilities, such as CVE-2023-34362 and CVE-2023-36934, are already being tested in the wild.
If your MOVEit Transfer instance is online and unmonitored, you may already be on an attacker’s target list.
Now’s the time to:
• Patch all known MOVEit vulnerabilities
• Limit public-facing access
• Monitor for scan activity and open ports
• Block IPs identified by threat intelligence feeds
• Harden file transfer environments and deploy honeypots if needed
Scanning isn’t random—it’s reconnaissance. Act now before scanning turns into breach.
Read the article for details: https://www.cuinfosecurity.com/scans-probing-for-moveit-systems-may-be-precursor-to-attacks-a-28832
More information on printer security, since they are often a cybersecurity blind spot!
Last week, we shared a warning about the unpatchable Brother printer vulnerability (CVE-2024-51978) that puts millions of devices at risk. If you haven’t updated your default admin passwords, do it now.
Since there was a lot of interest in this topic, we're sharing our classic, but still very relevant, on-demand webinar, "How I met your printer": https://youtu.be/b6d6RO2AFgw
@tompohl shares real-world techniques attackers use to exploit printers for initial access and lateral movement—exactly what we see in our penetration tests all the time.
If you haven’t tested your print infrastructure, now’s the time. Need help? Our pentest team can assess your network and highlight hidden vulnerabilities.
#Cybersecurity #CISO #PrinterSecurity #PenetrationTesting #LMGSecurity #NetworkSecurity #Infosec #ITsecurity
#penetrationtesting #pentest #pentesting
Are we securing AI like the rest of the cloud? https://www.helpnetsecurity.com/2025/06/30/chris-mcgranahan-backblaze-ai-cloud-security/ #Artificialintelligence #penetrationtesting #cloudsecurity #cybersecurity #Don'tmiss #Backblaze #Features #Hotstuff #News

Testing KALI Linux 2025.2 live ISO persistence USB mode.
Hundreds of Brother printer models are affected by a critical, unpatchable vulnerability (CVE-2024-51978) that allows attackers to generate the default admin password using the device’s serial number—information that’s easily discoverable via other flaws.
748 total models across Brother, Fujifilm, Ricoh, Toshiba, and Konica Minolta are impacted, with millions of devices at risk globally.
Attackers can:
• Gain unauthenticated admin access
• Pivot to full remote code execution
• Exfiltrate credentials for LDAP, FTP, and more
• Move laterally through your network
Brother says the vulnerability cannot be fixed in firmware and requires a change in manufacturing. For now, mitigation = change the default admin password immediately.
Our pentest team regularly highlights printer security as a critical path to system compromise—and today’s news is another example that underscores this risk. This is your reminder: Printers are not “set-and-forget” devices. Treat them like any other endpoint—monitor, patch, and lock them down.
Need help testing your network for exploitable print devices? Contact us and our pentest team can help!
Read the Dark Reading article for more details on the Brother Printers vulnerability: https://www.darkreading.com/endpoint-security/millions-brother-printers-critical-unpatchable-bug
We know GenAI is risky, so why aren’t we fixing its flaws? https://www.helpnetsecurity.com/2025/06/27/cobalt-research-llm-security-vulnerabilities/ #penetrationtesting #securityassessment #cybersecurity #GenerativeAI #Cobalt #report #News #LLMs
