In anticipation of installing NetBSD on a remote VPS next week, I've installed NetBSD today on a local device to poke around a bit!
#runbsd
New @bsdcan Video Posted:
The state of 3d-printing from OpenBSD by Andrew Hewus Fresh
@AFresh1
It's possible to do some 3d printing related things on an OpenBSD machine, but there are a bunch of popular tools that aren't available in the ports tree. We will talk about some of the different classes of software and what things are popular and whether they are currently available on OpenBSD and what the blockers are from getting those into the ports tree.
I recently installed NetBSD for the first time, on a remote VPS. All was fine, I installed pkgin, got some packages installed, installed openssh-portable, got my firewall rules set and so on. Having used FreeBSD and OpenBSD before it was a little different, but not too different.
Then one day, or rather late at night I found I needed to install some X11 sets and fired up sysinst. It being late, I did not read everything very carefully, but quickly found "re-install sets", "custom installtion", and then the X11 sets at the bottom of the menu. I selected them and started the installation.
It took a little longer than expected, and I noticed it was reinstalling base for some reason. No worries I thought, I hadn't touched that in the few days the system had been running, so it shouldn't be a problem.
Then when everything was finished, I noticed things were not working as expected. I think I managed to kill the sshd listening daemon and couldn't start it again. Then I noticed /etc/rc.conf was blank, so I had no network configuration, no sshd startup, no nothing. It seems /etc had also been replaced with defaults.
So by my lonesome, I had quite quickly managed to make quite a mess of things. Fortunately I did not reboot as was my first intuition when I found things weren't working. Sshd from packages required another script which had been replaced, the original sshd I had set to listen on another port which wasn't allowed through current firewall rules and so on.
Sorry for the boring ending, but it was all fully recoverable from my one ssh connection that fortunately didn't drop. Got network configured again, got firewall set up and started, got correct sshd started and so on. Then reboot, and all was good. Thanks to good documentation and easy configuration.
And that is why I #RUNBSD
Even being completely new to #NetBSD it was easy to recover.
I've re-tried sysinst after the fact, and now see base, /etc and so on will be re-installed by default if you don't uncheck them, so now I know.
The European *BSD event of 2025 is getting noticed!
https://www.netokracija.com/event/eurobsdcon-2025
Ako znaš čitati hrvatski, dobar si.
If you can't, you probably need to translate the article. 

Grab your tickets at https://tickets.eurobsdcon.org
For everything else, peek at https://2025.eurobsdcon.org/
More information is added all the time.
EuroBSDCon 2025 in Zagreb, Croatia
September 25-28, 2025
Flashy flashy - backing up has never been so pretty.
New @bsdcan Video Posted:
ABI stability in FreeBSD By ShengYi Hung
The FreeBSD project doesn't guarantee the ABI stability in major version. However, for the minor version, we also not fully guarantee. This cause maintaining a out-of-tree module (at least for Kernel module like VirtualBox) a big problem because module compiles from 14.0 may not able to use at 14.1. This also cause some problem when distributing modules with freshpkg in our base because our pkg system only support build for all major version.
A wiki page distribute the workflow of CTF diff and script:
https://wiki.freebsd.org/ShengYiHong/ABIStability?highlight=%28ABI%29
The outline of my slides will be as following:
What is ABI and why we needs to stablize ABI?
How to maintain ABI stability (a tool to check and ABI tag in binary)?
ABI information (CTF and dwarf) in elf and why we use CTF?
New tools CTFDiff: Why implement new CTFDiff and don't use the illumos one? (we port libctf and other command line tools like ctfdump to FreeBSD from illumos)
CTFDiff script: scripts download tarball from web (kernel tarball) so that we can compare abi between local compile one and web.
Short demo (maybe) for ctfdiff ?
Current status of CTFDiff (needs reviewers, licenses issue (CDDL))
Future works: regulize a stable function/obj ABI/API in kernel.
I have an idea for a new project blog, and discovering useful information about how to set one up with a cheap VPS running NetBSD courtesy of this post from @stefano ...
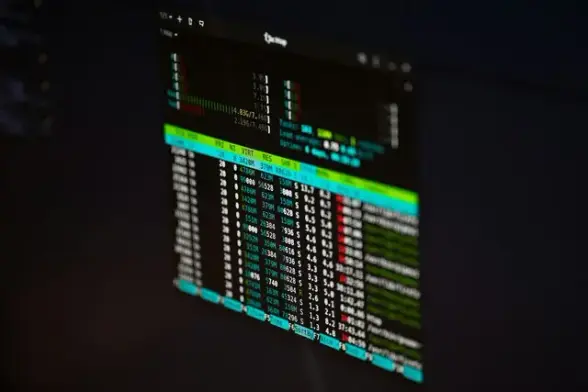
By the way, I'm having fun looking at some uptime data. Here's some:
%up 99.996 | since Wed Nov 22 10:51:03 2023
%up 99.998 | since Fri Jul 29 09:35:57 2022
%up 99.999 | since Wed Apr 6 14:48:49 2022
%up 99.931 | since Thu Sep 7 08:48:55 2023
%up 99.989 | since Sun Mar 20 18:06:40 2022
%up 99.994 | since Thu Dec 9 17:10:22 2021
In other words, they were only offline for updates that needed a reboot.
These are all leased production servers located in Europe, running FreeBSD with jails and VMs.
No need for Kubernetes or the cloud to get great uptime!

@BastilleBSD
Thank you #FreeBSD devs/contributors/admins/everyone-involved! 
Today we want to thank the #FreeBSD core team for all their hard work and contributions. 
Our favorite OS wouldn't be what it is today without their work.
Thank you!
So this is where my peeps at!
Hello everyone, my name is Børge and I am happy to get back into the BSD world, though only for personal projects for now.
I was a sysadmin for a small telco a while ago and we used Solaris/SPARC and FreeBSD/i386 for our servers, while I tried my hand at OpenBSD for my personal server. The network was all Cisco at the beginning, with some Juniper equipment for peering at the end but I did not get any experience with those unfortunately. I do have a certificate in SS7 somewhere, the signaling protocol telcos use for voice calls, but have forgotten pretty much all of it.
These days work is "cloud everything", which all seems to be based on Linux-something.
Reminiscing of "the good, old days" I wondered if I could run a BSD server anywhere to tap into my sysadmin background a little, or if I would have to use some Linux distribution.
Searching for BSD hosting providers, I am very happy I discovered #OpenBSDAms which I use for OpenBSD hosting (obviously).
Then I came across #BoxyBSD where I was lucky enough to get a FreeBSD instance.
Last but not least I came across a cheap VPS provider where I could run NetBSD. I don't mention the provider because I'm not sure I can recommend them yet.
I've been on Mastodon a little while, mostly reading as there is so much of interest to find here, though also because I'm quite shy, but hope to maybe post something about what I do now and then.
I really like all the *BSDs, they just do things in a way that seems sensible to me, so being here feels a lot like coming home.
So that's me a little about me. #introduction
How are you?
New @bsdcan video posted:
Controlled credentials transitions without privileges: mac_do(4), mdo(1) and setcred(2) by Olivier Certner
In this talk, we will present a project that aims at allowing controlled process credentials transitions without using setuid executables but instead leveraging FreeBSD's MAC framework.
Traditional credentials-changing programs, such as sudo(8), have a non-negligible attack surface as they often include a lot of infrequently used features and mechanisms that can be dangerous from a security standpoint (e.g., loadable modules). As these programs have to run as 'root', compromising them can have catastrophic consequences.
The mac_do(4) kernel module has been introduced to allow unprivileged processes to change credentials, provided the requested changes are explicitly allowed by rules set by an administrator. It has recently undergone major changes. First, thanks to a redesign of rules, it is now possible to specify full sets of user and group IDs that must be present or absent in the final credentials for a transition to be accepted. Second, each jail can be configured with a different set of rules, allowing different transitions to be allowed as needed, or to inherit from the parent jail.
We will describe how mac_do(4)'s credentials rules work, what the role of the mdo(1) companion program is, and what you can do with them in practice.
We will also touch on some aspects of the implementation, notably why we needed to introduce the new setcred(2) system call, which allows to change all process credentials in a single call, and possibly those that are related to the use of some FreeBSD's kernel sub-systems (notably, sysctl, jails and OSD).
While the current implementation is of production quality and immediately useful, there are lots of possible ways to extend it to cover more scenarios and to progress towards our ideal of having all credentials-changing programs work without the setuid bit. We will present them in the hope to get feedbacks.
I'd be adding stuff like collectd for monitoring using my home assistant too plus other stuff as I learn.
https://dl.dell.com/topicspdf/optiplex-3080-desktop_owners-manual6_en-us.pdf
#OoenBSD #RunBSD
A Self-hosted, BSD-native Gemini Protocol Server Stack - by @rqm@exquisite.social - @rqm@journal.bsd.cafe
For those who are adventurous enough to explore the non-http corners of the Internet, the Gemini protocol is a delightful experience to use. It has been around a number of years, making the biggest bang around the time when discontent with the web’s general demise started to reach current heights (so maybe around 2022).
https://journal.bsd.cafe/2025/07/22/a-self-hosted-bsd-native-gemini-protocol-server-stack/
#RunBSD