Efimer Trojan delivered via email and hacked WordPress websites
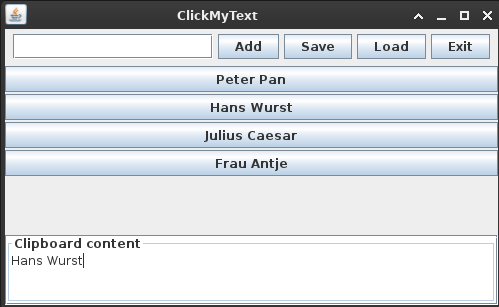
The Efimer Trojan is spreading through compromised WordPress sites, malicious torrents, and email campaigns impersonating lawyers. It steals cryptocurrency by replacing wallet addresses in the clipboard and can execute additional malicious scripts. The Trojan communicates with its command-and-control server via the Tor network. It has additional capabilities to brute-force WordPress sites and harvest email addresses for further distribution. The malware primarily targeted users in Brazil, India, Spain, Russia, Italy, and Germany between October 2024 and July 2025, affecting over 5,000 Kaspersky users.
Pulse ID: 689603fc3a16a87400a387ee
Pulse Link: https://otx.alienvault.com/pulse/689603fc3a16a87400a387ee
Pulse Author: AlienVault
Created: 2025-08-08 14:04:44
Be advised, this data is unverified and should be considered preliminary. Always do further verification.